Monitoring Onions
One of the first questions I had when Facebook launched their onion was “I wonder how stable it is?”. Tonight with some help from torsocks I am now monitoring availability of several onions, and trending all Nagios perfdata outputs from check_http, check_ssh, and check_tcp.
I’ve written a set of instructions and sample configurations for monitoring Tor hidden services (onions) using Nagios and put them in a public Github repository. check_commands for everything you need to monitor http, ssh, and other more generic tcp services on your onions is in the repo.
The process I went through to get working monitoring of onions was fairly simple, initially I was going to use proxychains, however torsocks turned out to be simpler. Basically I ran torsocks check_http -H onion; echo $? to check that torsocks passed the exit codes through, confirmed that it did, and then wrote out a set of check_commands and put them in my nagios configuration by simply copying the regular check and prepending it with /usr/bin/torsocks.
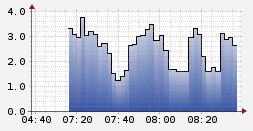
The load performance of Facebook’s https onion site after about an hour.

